To setup SSL in different java based web servers like Apache, Tomcat, Glassfish, we generally use the keytool command line to create certificate, generate CSR etc…, which is a bit complicated and confusing if you are not well versed with the keytool command line, We can make our life much more easier, by using Keytool IUI which is GUI version of keytool. We will be creating certificate, CSR and importing the response using keytool IUI for Glassfish Web server
Download KeyTool IUI : Here
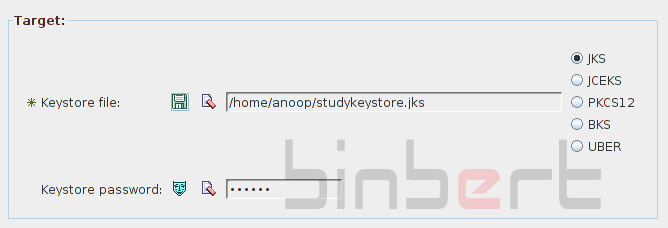
Create a keystore file
- Select window’s task Create empty keystore
ie. if not visible, use in the menubar:
View | Select task | Create | Keystore
give password changeit that is the default password of glassfish keystore.jks, it will be easy if you give the same password.
- Fill in the fields by clicking the respective icon buttons
==> once all required fields are filled, Action button (located at bottom) becomes enabled - Click Action button
Create a private key (keypair) entry, then save it in an existing keystore:
Trusted CA, private key (keypair) entry
ie. private key of type RSA.
This is done in 3 steps.
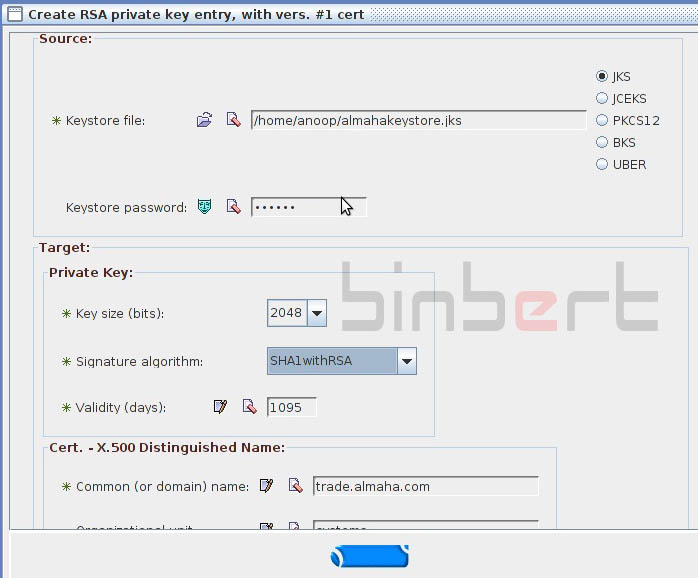
Step 1/3: create private key entry
- Select task Create RSA private key entry
View | Select task | Create | Keystore’entry | RSA Private key with vers, with #1 cert
- Fill in the fields
==> once all required fields are filled, Action button becomes enabled - Click Action button
==> A dialog shows up, containing the table of all available entries of the selected KeyStore - At the bottom of the dialog, enter new alias, enter password, confirm password
give alias name as s1as and password changeit this is the default alias name and password in glassfish, if you change the alias name and password the necessary changes has to be made in glassfish.
- Click OK button
Step 2/3: export CSR
- Select task Export certificate from private key entry as CSR file
View | Select task| Export | Certificate | CSR from private key entry
- Fill in the fields
==> once all required fields are filled, Action button becomes enabled - Click Action button
==> A dialog shows up, containing the table of all available entries of the selected KeyStore - Select the alias pointing to the right private key (the one that was created in step 1/3), enter the respective password
- Click OK button
==> This will generate a CSR file in PKCS#10 format. Submit this file to your CA (look for a CA that provides code signing certificate).
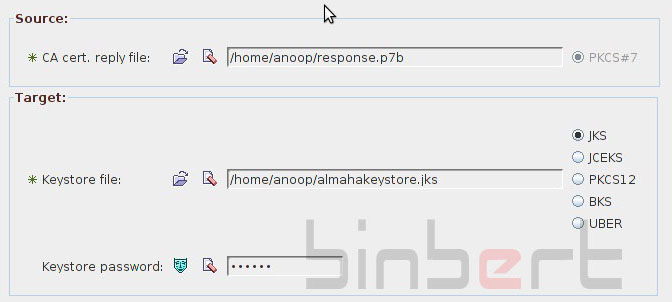
Step 3/3: import trusted certificate
Once your trusted certificate has been approved by the CA, you should receive it in PKCS#7 format (otherwise convert the one you get). Copy the content(response conent which you receive in your mail) to a file and give extension .p7b (ex-:response.p7b)
Important
We also need to integrate intermediate certificate from the CA,otherwise some browsers (firefox 3.5) will show error during validation and say it is not a trusted certificate. We can download the intermediate from the CA’s site (for example verisign intermediate can be found in https://www.verisign.com/support/ssl-certificates-support/install-ssl-certificate.html). Copy the intermediate certificate and merge it with the response file, and then import to the keystore
How to
1. create file response+intermediate.p7b
2. Open response+intermediate.p7b file in vi, notepad or any other file editing tools
3. Copy the response file content send by your CA and paste it to the file (response+intermediate.p7b)
4. Copy the intermediate file content from CA site and paste it in the file (response+intermediate.p7b)
5. Now the response+intermediate.p7b file will be having two set of key’s, one is the response given the CA and the Intermediate taken from the CA website
6. Continue to the next step to import the response+intermediate.p7b file to keystore.jks
- Select task Import CA certificate reply to private key entry
View | Select task| Import | Certificate | CA cert. replay to private key entry
- Fill in the fields
==> once all required fields are filled, Action button becomes enabled - Click Action button
==> A dialog shows up, containing the table of all available entries of the selected KeyStore - Select the alias pointing to the right private key entry (the one that was created in step 1/3, and used in step 2/3), enter the respective password
- Click OK button
==> This will import your trusted CA in the respective private key entry.
Now your keystore file is ready to deploy in glassfish. Copy the keystore file to server SDK/domains/domain1/config folder
restart the glassfish server, and take the url
copy, delete, change alias or/and password, …
- Change keystore’s password,
- Change secret/private key entry’s password,
- Change entry’s alias,
- Delete entry,
- Copy entry,
- View trusted certificate entry,
- View private key entry’s certificates chain,
- View secret key entry’s infos.
==> Open up KeyStore manager.
ie. from the menubar:
Tools | Keystore manager| [keystore-type] (JKS keystore) keystore … (file name)
 Binbert Technology | Computer | Security | Networking | Mobile
Binbert Technology | Computer | Security | Networking | Mobile